Principle: Hardware matters
It is easy to underestimate the underlying structure of our digital world.
Back to Basics
There are innumerable examples of average people being unable to explain how the modern conveniences of their life work. From creating food, energy, and products to what it takes to make them accessible, nearly everyone is quite ignorant about these things. In an age of such rapid transformation it is quite understandable if not predictable. When it comes to technology, almost everything is quite obscured for a person who doesn’t take the time to look.
This creates a great deal of confusion and friction when trying to truly decentralize power. In most cases, it’s not always necessary for someone to know details about every service and system they use. However, there are many advantages to being aware of some fundamental elements of digital systems that surround us. We as people working to safeguard and expand human liberty, must at least understand the basics of how things work.
Hardware
In their simplest form, computers use power to run computations on signals. They can use those signals to manipulate devices to do all kinds of things like run displays or store information. These devices can have ways to collect information and signals for the computer. With more sophisticated programming we can use these signals to create files and media, access the web, and enjoy a large variety of multimedia content. When it comes to any device you have, you’ll at least want to be aware of what it can do.
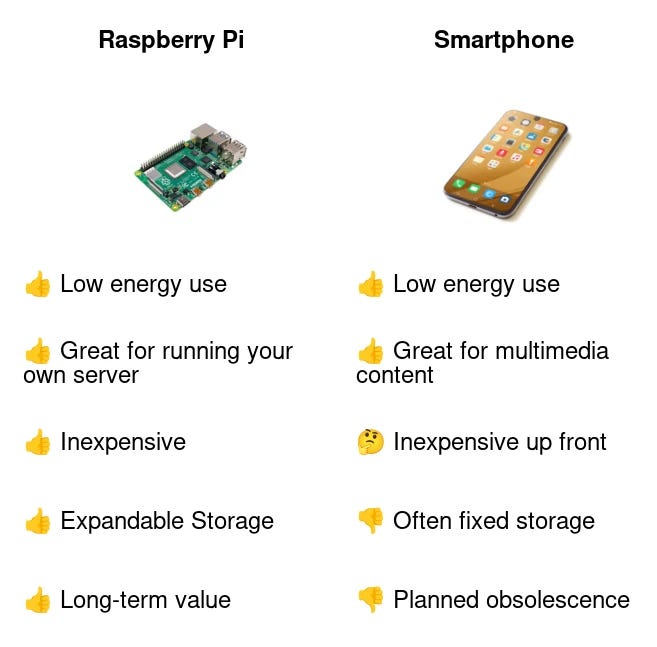
Specialized hardware
One cpu = one vote
One of the things that initially got me excited about Bitcoin was that it created a market incentive for people to acquire more powerful computing. I had hoped that this would eventually decentralize computing power across society. That was quickly demolished when specialized hardware was created uniquely for the purpose of mining Bitcoin. There are also specialized devices for machine learning and authentication. using specialized hardware can do wonders for resource efficiency and simplifying problems.
Unfortunately that also means that general computing devices could end up being restricted from the people. If all kinds of functions are available through cloud providers and specialized products, bad actors could argue that general-purpose computing is too dangerous to be accessible to the masses. General purpose devices would likely consume more resources, and these “wasteful” devices could be restricted in the name of conserving energy.
What happens when we ignore hardware?
There’s no reason to guess because in many ways we already have. Smartphones are the perfect representation of what happens when we aren’t in control of our computing. People’s own devices and data can become weaponized against them.
The cloud
There is no cloud, there is only someone else’s computer
By putting all of your data on cloud services you have no idea where the data is actually stored and if it is truly protected. While the best way to protect data is to never record it, a great way is to only store it on your own devices. While many cloud providers boast stringent security, data breaches are an all-too-common occurrence. By keeping your data to yourself, it is safer because you’re likely to be less of a target than everyone’s cloud data combined.
“Serverless”
Why use your own devices at all? Why not simply centralize all computing power and storage into one giant big iron. Due to the economies of scale, it can be tempting to reap the efficiency gains of using massive supercomputers as a common good. While for some applications this may be quite viable, the name “serverless” is entirely misleading. All the computation and storage still needs to exist somewhere. Whoever, or whatever has control of that mainframe is effectively the master of the resource. Bad actors would be highly motivated to corrupt and manipulate that resource, undermining any efficiency gains from centralization.
If you’re sincerely interested in running systems without servers at all, you may be interested in gun.js. Gun is a useful framework for building peer-to-peer persistent applications. These applications effectively store all the important data among the users.
Rebuilding
All three primary resources in cyberspace (Computing power, Storage, & bandwidth) are entirely reliant on hardware. This means if you’re hoping to democratize our online experience, you want to ensure those three (and the hardware that supports them) are as decentralized as possible. While it may be impossible to perfectly decentralize these things, incremental progress can yield exponential results.
Free (as in Freedom) hardware
It is a mistake to continue to buy hardware from large corporations with an incentive to sell you cloud services. You can’t reasonably expect that they will chose principles they don’t have over their bottom-line. Ideally your hardware would be entirely sourced from local, ethically built, businesses that respect your freedom. Unfortunately we are quite far away from that being the standard. It is our responsibility collectively to remove unnecessary barriers to making that a reality.
The Free Software Foundation has a fantastic campaign called Respects your freedom or hardware that meets their certification
Other initiatives
Regardless of what we choose, it’s important that we get better at supporting hardware designers and manufacturers that support freedom.



Yes, believe it is possible to use digital technology in a positive way but we have not used much of our technology in a positive way so far. Is our history our destiny or can we truly heal ourselves? I attempted to write about some of this in previous posts.
https://open.substack.com/pub/kwnorton/p/is-the-universe-hostile-to-computers?r=boqs0&utm_campaign=post&utm_medium=web